Security issues in a WAN can differ compared to security in a LAN. In a LAN, most devices can be under the control of the organization owning the devices. Traffic between devices in the same building might not ever leave the confines of the office space used by that company. However, with WANs, by definition, the traffic leaves one location and travels through some other network owned by the service provider and back into another site.
The term authentication refers to a set of security functions that help one device ensure that it is communicating with the correct other device. For instance, if R1 and R2 are supposed to be communicating over a serial link, R1 might want R2 to somehow prove that it really is R2. Authentication provides a way to prove one’s identity. WAN authentication is most often needed when dial lines are used. However, the configuration of the authentication features remains the same whether a leased line or dial line is used.
PAP and CHAP
Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP) authenticate the endpoints on either end of a point-to-point serial link. CHAP is the preferred method today because the identifying codes flowing over the link are created using a Message Digest 5 (MD5) one-way hash, which is more secure than the clear-text passwords sent by PAP.
Both PAP and CHAP require the exchange of messages between devices. When a dialed line is used, the dialed-to router expects to receive a username and password from the dialing router with both PAP and CHAP. With a leased line, one router starts the process, and the other responds. Whether leased line or dial, with PAP, the username and password are sent in the first message. With CHAP, the protocol begins with a message called a challenge, which asks the other router to send its username and password. The schematic below outlines the different processes in the case where the links are dialed. The process works the same when the link uses a leased line.
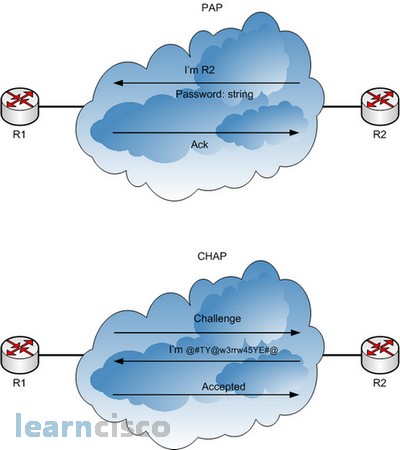
PAP flows are much less secure than CHAP because PAP sends the host name and password in clear text in the message. These can be read easily if someone places a tracing tool in the circuit. CHAP instead uses a one-way hash algorithm, with input to the algorithm being a password and a shared random number. The CHAP challenge states the random number; both routers are preconfigured with the password. The challenged router runs the hash algorithm using the just-learned random number and the secret password and sends the results back to the router that sent the challenge. The router that sent the challenge runs the same algorithm using the random number (sent across the link) and the password (not sent across the link). If the results match, the passwords must match. The most interesting part of the process is that at no time does the password itself ever cross the link. With the random number, the hash value is different every time. So even if someone sees the calculated hash value using a trace tool, the value is meaningless as a way to break in next time. CHAP authentication is difficult to break, even with a tracing tool on the WAN link.
Here followes an example of configuring CHAP between routers R1 and R2, which are connected through serial communication on their serial 1/0 ports.
Router R1
R1(config)#int se 1/0
R1(config-if)#
R1(config-if)#encap ppp
R1(config-if)#ppp authentication chap
R1(config-if)#exi
R1(config)#
R1(config)#username R2 password s3cr3t
Router R2
R2(config)#int se 1/0
R2(config-if)#
R2(config-if)#encap ppp
R2(config-if)#ppp authentication chap
R2(config-if)#exi
R2(config)#
R2(config)#username R1 password s3cr3t
R2#ping 10.0.0.1Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 32/84/168 ms
R2#
Notice that each router refers to the other router’s host name; each router uses its own host name in CHAP flows unless overridden by configuration. Each side configures the same password.
Our Recommended Premium CCNA Training Resources
These are the best CCNA training resources online:
Click Here to get the Cisco CCNA Gold Bootcamp, the most comprehensive and highest rated CCNA course online with a 4.8 star rating from over 30,000 public reviews. I recommend this as your primary study source to learn all the topics on the exam.

Want to take your practice tests to the next level? AlphaPreps purpose-built Cisco test engine has the largest question bank, adaptive questions, and advanced reporting which tells you exactly when you are ready to pass the real exam. Click here for your free trial.
