Extended IP access lists have both similarities and differences compared to standard IP ACLs. Just like standard lists, you enable extended access lists on interfaces for packets either entering or exiting the interface. IOS searches the list sequentially. The first statement matched stops the search through the list and defines the action to be taken. The one key difference between the two is the variety of fields in the packet that can be compared for matching by extended access lists. A single ACL statement can examine multiple parts of the packet headers, requiring that all the parameters be matched correctly in order to match that one ACL statement. That matching logic is what makes extended access lists both much more useful and much more complex than standard IP ACLs.
Here are shown several of the fields in the packet headers that can be matched.
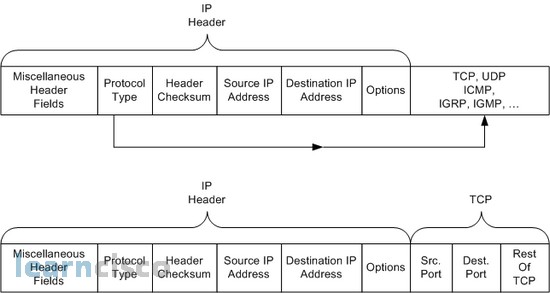
The top set of headers shows the IP protocol type, which identifies what header follows the IP header. You can specify all IP packets, or those with TCP headers, UDP headers, ICMP, and so on, by checking the Protocol field. You can also check both the source and destination IP addresses, as shown. The lower part of the figure shows an example with a TCP header following the IP header, pointing out the location of the TCP source and destination port numbers. These port numbers identify the application. For instance, web uses port 80 by default. If you specify a protocol of TCP or UDP, you can also check the port numbers.
IOS checks all the matching information configured in a single access-list command. Everything must match for that single command to be considered a match and for the defined action to be taken. The options start with the protocol type (IP, TCP, UDP, and others), followed by the source IP address, source port, destination IP address, and destination port number. Remember that the port numbers can be referenced only if the protocol type is configured as TCP or UDP.
The sequence of the parameters in the command affects exactly what the IOS ACL logic examines in the packet when trying to make a match. When configuring an ACL to check port numbers, the parameter in the access-list command checks the source port number when the parameter is placed immediately after the source IP address. Likewise, the parameter in the access-list command checks the destination port number when the parameter is placed immediately after the destination IP address. Depending on where you enable an extended ACL, and for which direction, you might need to check for the source or destination port number.
Configuration
The following table lists the configuration commands associated with creating extended IP access lists.
| Command | Description |
|---|---|
| access-list access-list-number {deny | permit}protocol source source-wildcard destination destination-wildcard [log | log-input] | Global command for extended numbered access lists. Use a number between 100 and 199 or 2000 and 2699, inclusive. |
| access-list access-list-number {deny | permit} tcpsource source-wildcard [operator [port]] destination destinationwildcard [operator [port]] [established] [log | log-input] | A version of the access-list command with TCP-specific parameters. |
| access-list access-list-number remark text | Defines a remark that helps you remember what the ACL is supposed to do. |
| ip access-group {number | name [in | out]} | Interface subcommand to enable access lists. |
| access-class number | name [in | out] | Line subcommand for standard or extended access lists. |
| show ip interface [type number] | Includes a reference to the access lists enabled on the interface. |
| show access-lists [access-list-number | access-list-name] | Shows the details of configured access lists for all protocols. |
| show ip access-list [access-list-number | access-list-name] | Shows IP access lists. |
In the following case, Bob is denied access to all FTP servers on R1’s Ethernet, and Larry is denied access to WWW Server’s web server. We will use the picture from the previous page as a reminder of the network topology. The following example shows the configuration on R1.
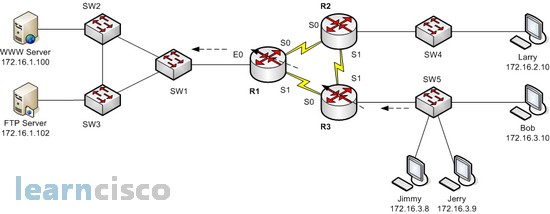
!
interface Serial1/0
ip address 172.16.12.1 255.255.255.0
ip access-group 110 in
serial restart-delay 0
!
interface Serial1/1
ip address 172.16.13.1 255.255.255.0
ip access-group 110 in
serial restart-delay 0
!
...
!
access-list 110 remark Stop Bob to FTP Server and Larry to WWW Server
access-list 110 deny tcp host 172.16.3.10 172.16.1.0 0.0.0.255 eq ftp
access-list 110 deny tcp host 172.16.2.10 host 172.16.1.100 eq www
access-list 110 permit ip any any
!
Our Recommended Premium CCNA Training Resources
These are the best CCNA training resources online:
Click Here to get the Cisco CCNA Gold Bootcamp, the most comprehensive and highest rated CCNA course online with a 4.8 star rating from over 30,000 public reviews. I recommend this as your primary study source to learn all the topics on the exam.

Want to take your practice tests to the next level? AlphaPreps purpose-built Cisco test engine has the largest question bank, adaptive questions, and advanced reporting which tells you exactly when you are ready to pass the real exam. Click here for your free trial.
