Some people will call them “ackles”, some people call them access control lists, or ACLs. Those are all perfectly good names for these. These are tools, they are about identifying traffic. We construct a list of statements that say, here’s a set of parameters that I want to look for and here’s the action that I will take. It’s either permit or deny, so a deny sounds a good drop and that’s what it would do. Permit, send it on its way and these are tools that are used on routers, they are used on switches, they are used on firewalls.
This is the time and also the place to pick up access control lists because the further you go in Cisco, the more you will have used and taken advantage of the key skills that we teach you here. Wildcard masking is one of the things that we will look at. We have very proprietary, very advanced, and extremely powerful mechanisms for teaching you wildcard masking, they are exam relevant, they are real world relevant, and so you are going to get a lot out of this lesson.
ACL operation
Before we can get to wildcard masks and the overall syntax of access control lists, we have to understand their operations. Spend a moment staring at this diagram and then allow your heart rate to slow down.
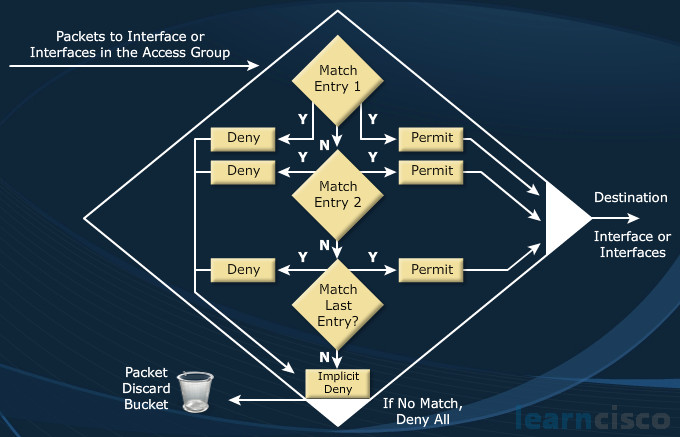
When I see diagrams like these, I panic a little bit because they can be complicated. They can be a little convoluted as you’re trying to follow the yeses and the nos, and the triangles and the errors. So we follow these arrows and what does all this mean? Well don’t panic, look bellow and check the access control list rules of engagement:
- Top Down Processing
- Immediate Execution Upon A Match
- Implicit Deny Any At the End
These three steps summarize everything we see happening on the scheme above. All jokes aside, let’s look at these three roles. The first one – if it’s a list of statements, it’s a set of logic and think about programming logic for a moment. When we are programming, there’s a proper way to go through all of the logic and we have the same thing here. If we have 15 entries on an access list or just one, the minimum, one would be the minimum, we wouldn’t have to worry about order so much. But if we have 15, we go through top-down, which means the earliest entries are processed first.
What I mean by that is, when the entries in an access control list are input by you, the administrator or someone else, the very first one that they put into this access control list would be the earliest and therefore the topmost. And then the second to be entered would go down further. And the most recently issued entry would be at the very bottom and that controls the order in which they are processed, so we go sequence 10, sequence 20, sequence 30 and they are sequenced. And let’s say I didn’t find a match for sequence 10, I did find a match for sequence 20, what then does that mean once I have quote “matched a sequence”?
Well we immediately execute upon that match, what do we mean by that? I will go as deep as I need to in the access control list, but once I find an answer to my question, I don’t process anything deeper. That’s right, you stop right there. You do what it says and you don’t continue looking. Now I’ve got a question for you folks, maybe you are a science buff and there’s this thing out in the cosmos. In fact, there are many of them, they are superdense, they are sometimes called singularities. What they do is they suck in all light, they suck in all light, nothing can escape them unless you are really deep into physics and you realize something is going to escape them. But again I digress. What’s that thing that I’m describing there, where no light can leave? So a collapse star, it’s a black hole, right? What’s a black hole to us in an access controller?
Well when it comes to our access controllers, that black hole occurs at the end of our list, so we have this list with entries, we are going down through these entries. What if we don’t have a match, what happens at that point? Do we allow the traffic through, do we deny it? We need something at the end of the access controllers to gobble everything up, that black hole and we refer to that as the implicit deny any, implicit deny any, never forget that. Here’s what happens – if you do not match an entry in that access control list, you get gobbled up by that implicit deny any.
And what does it say, deny, it means you don’t match, you are denied, you are not getting through. Do we see this in the access control list, is there an entry that says this is the implicit deny any entry? Well, let me ask you, do you see black holes? The answer is no, you don’t see black holes nor do you see the implicit deny any. Implicit is not an everyday word, is it? At least not, not in a circle of people that I run with, but you could swap out the word implicit with invisible and it would work just as well, it’s the invisible deny any sitting at the end gobbling up everything that touches it, everything that reaches the very end.
So it’s like falling off a cliff and let’s not lose sight of the fact that these three rules govern all of the behavior of an access control list. When we’re mindful of this, top-down processing, immediate execution upon a match, the implicit deny any, then all we need to understand is things like syntax and making that syntax deliver the ultimate goal that we are intending.
Our Recommended Premium CCNA Training Resources
These are the best CCNA training resources online:
Click Here to get the Cisco CCNA Gold Bootcamp, the most comprehensive and highest rated CCNA course online with a 4.8 star rating from over 30,000 public reviews. I recommend this as your primary study source to learn all the topics on the exam.

Want to take your practice tests to the next level? AlphaPreps purpose-built Cisco test engine has the largest question bank, adaptive questions, and advanced reporting which tells you exactly when you are ready to pass the real exam. Click here for your free trial.
