Enumeration, fingerprinting, spoofing
Two of the most common ways to figure out information about a network or to do information gathering is enumeration and fingerprinting, and ping sweeps which are basically going to run through a series of IPv4 and IPv6 addresses to find out what’s being used, as well as port scanning for user unused TCP and UDP ports will help you identify the services that are being used in the networks and the ones that aren’t being used. You can also identify which ones are being filtered out as well, that’ll give you information. You can identify all the hosts and their IP addresses, you can also find out information from the MAC address. For example, as to what type of, let’s say, laptop it is or workstation. Sometimes by knowing what vendor’s organizational ID is assigned to a network interface card, you can combine that with other information to identify operating systems, you can also be able to look for different vulnerabilities. A very common one is a ping sweep. This is basically ICMP echo request or pings sent to a number of hosts and if that particular address is live, they’ll get an ICMP echo reply. We’re trying to look for hosts that are available on the network, then we can further prob them for vulnerabilities, probably name it Layer 4 and above. Now ping sweeps aren’t actually the most effective way and there are lots of countermeasures against this, they’re old and slow, okay, but there are other more effective ways to scan a network.
Spoofing is the process of introducing a fake IPv4 usually address into a communication, also you can spoof MAC addresses as well. You’re basically using a fake device address. Now this can be done to impersonate or masquerade as a legitimate host on the inside corporate LAN, but it can also be spoofing so that when a particular server sends error messages or floods error messages back to the sender, it’s actually not going to the sender, it’s actually going to some spoofed IP address which is the actual ultimate target. So you’re kind of using that router or server as the one to launch the attack because it’s sending a bunch of error messages. So this can use trusted internal addresses or it can use external IP addresses. Like we mentioned MAC addresses are also spoofed in switched environments as well.
Now why do we spoof? Well, we’re trying to get root access by masquerading as a legitimate host, we’re trying to inject malicious data or malicious commands into a data stream, we’re trying to divert network packets back to the hacker or the cracker, we’re trying to implement denial-of-service attacks by crashing servers, or it’s a step in a larger attack, because the IP-spoofed address is the actual target that we’re going to flood with error messages from a server or router.
Blended threats and identify theft
Typically the enumeration and fingerprinting stuff are really the part of the early phases of information gathering. The actual exploit will be done using often a complex collection of malware that will infect, that will propagate, and then send its payload using different techniques, for example Buffer Overflows. These are known as blended threats, and they can combine characteristics of viruses, worms, spyware, and Trojan horses to do their damage. Most of these blended attacks are considered zero day, which means they have been identified by Trend Micro, or Cisco, or one of the other antivirus companies. These blended attacks are always evolving. Some of these are extremely complicated and long term like advanced persistent threats against large government infrastructure or corporations. They’ve been pretested by cyber criminals, and they can easily breach firewalls and intrusion prevention systems and are really a huge challenge for detection and countermeasure.
Here are a couple of terms you want to define. First of all, we have phishing, which is typically an exploit that’s done through E-mail or instant messaging where someone’s masquerading as an actual entity, a trustworthy entity like a bank or a brokerage firm, for example. They’re basically trying to get sensitive information or steal your identity. They’re trying to get credit card details, Social Security Numbers, usernames, passwords – those types of things. So it could be done with the fake E-mail that looks legitimate, they will kind of direct you to a phony website, they can even attempt to do some phone contact by having you call a phone number. This is a social engineering attack, and it’s one of the primary methods for stealing identities.
Pharming is basically when you get redirected to a website or to another website that’s an exact mock up of the original. Basically, you change the host file on victim computers or you exploit the DNS server. This is a huge problem for e-commerce businesses and online banking websites, another way for hackers to try to steal your identity.
Man-in-the-Middle attacks
A man-in-the-middle (MitM) attack is also referred to as a meet-in-the-middle attack – which probably is a little bit more politically correct, but it can do several bad things to your network. It can be used to steal information, it can be used to hijack ongoing UDP flows or TCP sessions, especially get access to protected network resources. It can be used to analyze traffic, part of a reconnaissance to determine more information about your network and your individual users. It can be part of a denial-of-service attack, it can capture the information, it can corrupt it, and then it can reinject it back into the flow. In other words, it can break down your trust identity to modify traffic in a malicious way. It can also introduce new information into network sessions.
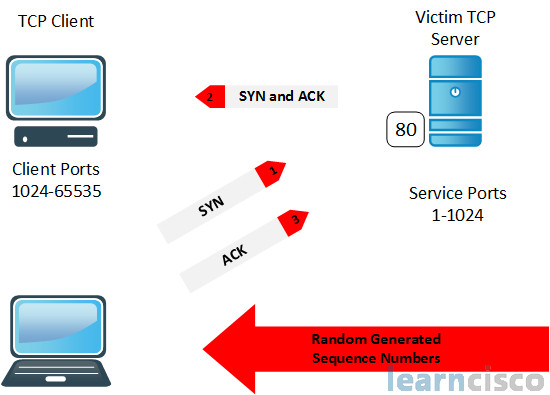
Now there are a couple of differentiations here – you have a blind attack and a non-blind attack. A blind attack will basically interrupt a connection that’s not crossing your cables. A non-blind attack interferes with connections that are crossing your cables, okay, or through the airways with wireless. A common variant of this is the TCP session hijack where the cracker will sniff to find out the client and server IP address and port numbers, and then modify the packet headers to spoof the TCP/IP packets from the client, and then wait for an acknowledgement packet from the client going to the server. That ACK will have the sequence number of the next packet that the client is expecting, they can reply using a modified packet with a source address of the server and the destination address of the client. So you’re basically forcing a TCP reset that disconnects legitimate client, the cracker then takes over the communication with the server by spoofing the expected sequence number from the acknowledgement previously sent from the legit client to the server. This could also be an attack against confidentiality if they’re able to break down weak keys, for example used in symmetric key encryption.
Confidentiality and integrity violations
Now I mentioned that a man-in-the-middle attack can also be used to conduct a confidentiality breach. And this is really when somebody gets access to read sensitive information that they’re not authorized to read. These are hard to detect because the hacker can basically copy this data without the owner’s knowledge and really without leaving a trace. Now this can be due to poorly-configured file protections, maybe somebody has global read access for example. And if the user has no reason to suspect this unwanted access or a breach of confidentiality, the audit will never be done, okay, so it’s really hard to know this is going on.
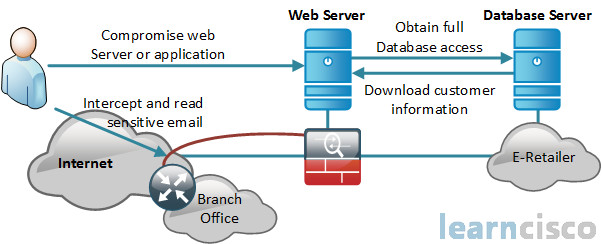
Here in our diagram, the cracker is trying to compromise an exposed web server. It uses a server as a beachhead to get full access to the database server in this front and backend solution. The cracker then uses the information from the database to intercept and read sensitive E-mail messages that are being sent to a user in a branch office. This is hard to notice because the cracker doesn’t modify or delete any data, they’re only reading it, okay, and they can use a wide variety of methods to compromise confidentiality. They can use ping sweeps and port scans, they can use packet sniffers like Wireshark for example or omnipeek. They can do emanations capturing where they’re capturing electrical transmissions from the actual equipment itself or from the wires. They can use overt channels that hide information in a transmission channel based on tunneling one protocol inside of another, or they can use covert channels where they hide information based on encoding data using another set of values. They can do social engineering methods. They can even do dumpster diving which is actually a type of social engineering going through your trash can or dumpster looking for phonebooks, org charts, memos, any kind of documentation that has information that could be valuable to a cracker. They could do wiretapping, and of course, they can do the aforementioned phishing and pharming to redirect users to websites or other links to get access to information. Typically, these are going to be doing more than compromising confidentiality, they’ll also be parts of attacks on integrity and availability of systems as well.
Now I’ve mentioned overt and covert channels as a way to compromise confidentiality. It’s based on tunneling one protocol inside of another, that’s overt. The covert channel is basically encoding data using some other set of events. So with the covert channel, the hacker is installing a Trojan horse on a target host. The Trojan can be written to send binary information back to the server of the cracker. For example, the client pings the server of the cracker once every minute, and that’s a zero, and two pings per minute represent a one. Now obviously, that can take a long time to get that message sent, but again some of these individuals they’re in it for the long haul. There are other quicker ways to do covert channels as well. What if ICMP is not allowed through a firewall, well you can have a client visit a webpage of the cracker, one visit per day would be a one and no visits would be a zero, that’s a covert channel.
Trust exploitation and password attacks
Now a trust exploitation is actually taking advantage of a trust relationship typically between servers on a network, more specifically within their directory system or something like Active Directory. And this can be best be mitigated with an advanced technique that you’re going to learn later on in your Cisco career known as private VLANs. But let’s look at an example of a trust exploit.
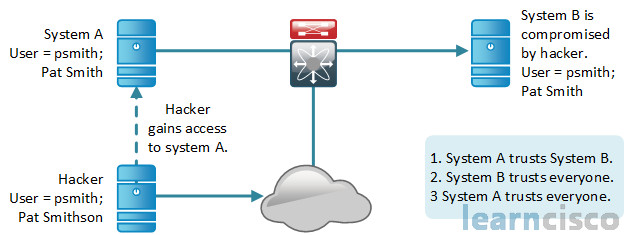
Basically, you have a system in the DMZ which is basically set apart for public servers, that would be System B in the diagram here. It has a trust relationship with the system on the inside of the firewall. So System B could be a frontend server and System A could be the backend database server like SQL, or MySQL, or maybe it’s a Microsoft exchange system where you have a server in the DMZ and the rest of exchange inside the firewall. So the hacker or cracker on the outside compromises System B in the DMZ. They can then leverage that trust relationship that System B has with System A to get access to System A. Again this can be based on Windows domains or Active Directory, other directories like LDAP for example, Linux and UNIX have the Network File System – NFS – or Network Information Service Plus – NIS plus. Those can all be compromised, and again you’ve to be very aware of that and configure our firewalls properly and effectively.
Now as a security practitioner, one of the main areas you have to deal with is protecting your access control mechanisms, and the most common will be password credentials, usernames and passwords, and so you need to be aware of password attacks. They can use many different approaches. They can do brute force where they just try every possibility with all the ASCII or Unicode characters, you can have Trojan horse programs that can capture passwords. There’s key loggers, this is a program that can be installed on an end host that actually logs the keystrokes on your keyboard. Again IP spoofing and packet sniffers can also determine usernames and passwords, and really what we’re trying to find out is the cracker has not just the password but also the username as well, okay, if they can find both, even better.
Now a brute force attack is basically using a program like Cain & Abel or Jack the Ripper, using it across the network and trying to login to a shared resource like a server by just basically trying every possibility it can. And once it gets access, it’ll try to escalate those privileges to be a route or administrative user. Any password stored in plain text is going to be an issue, so you really should encrypt your passwords to overcome these risks. For example, through a one-way MD5 or SHA-1 hash. So during the login process, when you supply your account and your password, the password encryption algorithm generates a one-way hash. By the way this is what happens when you go to the ATM machine and you put in your PIN – let’s say your four digit PIN number, that’s going to be cryptographically hashed. Hackers will use word lists of common words and phrases. They’ll use the brute force attack which could take a long time, but again some of these crackers are in it for the long term, sometimes they mix techniques or they use a combination of word lists and brute force. Anything that uses user authentication is vulnerable, if you’re using NetBIOS, or FTP, or Telnet, or SNMP, or PPTP, or terminal services, or Remote Desktop Protocol, any of those things can be sending credentials in clear text.
Availability violations
Now we mentioned that CIA of security – Confidentiality, Integrity, and the third A is Availability. Availability can be compromised with denial-of-service attacks and more advanced distributed denial-of-service attacks. The basic goal here is to overwhelm servers, overwhelm services, interrupt business processes, and cause problems between you and your customers.
DoS attacks typically happen because there is a failure in an application or a host to respond to certain situations in malicious code, maybe maliciously formatted input in a web form or some database frontend application. Also the inability of a network, or an application, or a server, or a host to do with enormous flooding of data, which can bring the system to a halt. Hackers use a lot of techniques to compromise availability. One of the most common is to use botnets which use a wide variety of channels to create kind of zombie hosts that can be remote controlled from servers. Sometimes there are consortiums of malicious crackers, there are denial-of-service attacks, there are more advanced distributed denial-of-service attacks. They can do flooding by flooding with the TCP synchronization process, the SYN packet, ICMP flooding. They can also compromise electrical power or the environment, humidity, heat, things like that.
Botnets
Let’s talk more about botnets. When we use the term botnet, the bot itself is the compromised system, it is the zombie computer that’s controlled by crackers. So running of this is automatic, okay. A botnet is a group of bots or a collection of compromised systems that are running malware like worms, Trojan horses, or backdoor code under a common command and control infrastructure from some, you know, criminal organizations, some criminal syndicate, it could be state-based, okay. And basically the originator will remotely control these bots using something like IRC – Internet Relay Chat, even though there are other channels that can be used to create a botnet. The bot typically is run hidden and you create a connection from an inside host back through your perimeter devices, your firewalls, your security routers, back to some fully qualified domain out on the Internet often in some other country. Some of the largest botnets have been recently brought down. Some of these can be huge like a 1.5 million node botnet was recently brought down. Some people estimate that up to 25 percent of all PCs are participating in some sort of botnet.
DoS and DDoS Attacks
Denial-of-service attacks are ubiquitous. They’re ongoing and service providers are constantly under these types of attacks, and they’re really difficult to eliminate, and most service providers will just simply throw more bandwidth at the problem. They’re getting a large number of requests over the Internet, and it can be trying to attack their routers, their servers, and so on. Now DoS attacks are different, they’re not trying to get access to your network, they’re not trying to get access to information on your network. They’re basically trying to make services and applications unavailable for their typical use. So they will exhaust CPU cycles, they’ll use up RAM, they’ll fill up page files on servers, they’ll overwhelm routing buffers on interfaces, they can also be used to deny services with IDS or IPS sensors that are trying to do their job. So there’s all different types of denial-of-service attacks, some of them are kind of trivial, some of them are extremely dangerous; for example, the DDoS attack, which is a much higher level of flooding traffic and it distributes it from a single machine to an entire network. So it’ll use a bunch of compromised machines that have remotely-controlled agents or zombies. So DDoS attacks are kind of like a bot, a botnet, okay. You’ve got a master control mechanism that is directing and controlling that. So what you can, you could consider a bot almost like an advanced form of distributed denial-of-service attack. However, the botnet of course is trying to leverage the connection from that compromised host back to the darknet or back to the servers. So you can consider DDoS attacks, the next generation of DoS attacks, and what we see now are more advanced tools than that because a lot of the firewalls and the sensors are aware of the most common distributed DoS tools, so they have countermeasures built into them.
Our Recommended Premium CCNA Training Resources
These are the best CCNA training resources online:
Click Here to get the Cisco CCNA Gold Bootcamp, the most comprehensive and highest rated CCNA course online with a 4.8 star rating from over 30,000 public reviews. I recommend this as your primary study source to learn all the topics on the exam.

Want to take your practice tests to the next level? AlphaPreps purpose-built Cisco test engine has the largest question bank, adaptive questions, and advanced reporting which tells you exactly when you are ready to pass the real exam. Click here for your free trial.
