Here we see some key terms for implementing our security policy or our security design.
- Defense in depth
- Compartmentalization
- Least privilege
- Weakest link
- Separation and rotation of duties
- Hierarchically trusted components and protection
- Mediated access
- Accountability and traceability
The foremost of these is defense-in-depth, where you’re going to have redundancy of technical controls and security controls. You’ll have multiple layers – kind of like protecting a medieval castle. Architectures are based on end-to-end security with for example, perimeter security through secure routers, and then maybe behind that firewall systems – which include the stateful packet filtering and Deep Packet Inspection, also IDS or IPS sensors using proxies or application layer gateways, then even having hardened multilayer switches behind that.
There is also compartmentalization where you create different security zones, and then you apply policy between those zones or between those modules; for example an outside zone, an inside zone, a DMZ zone, an intranet zone, your management VLAN zone, and of course, the datacenter server farm.
There is also the least privilege principle, which basically comes from the military and it is the need-to-know approach. You should only have the access or privilege to do your job and nothing beyond that, okay. You only have authorization to access services and take actions that you need to do for your job role and nothing more. Everything else by default is going to be denied.
Then we have the fundamental weakest link concept, which means your security system is only as effective or efficient as its weakest link, and unfortunately, humans are most often the weakest link.
There is also a separation and rotation of duties. So to countermeasure collusion and theft and other types of criminal behavior – fraud for example and error – you want to separate duties. It takes more than one person for example to sign a check over $500 – that kind of thing. And rotation of duties where one individual person doesn’t work on the same application or service or department on an ongoing basis. They get rotated in and out on a regular basis.
The hierarchical trust components and protection is compartmentalizing, coming up with server systems that can’t be compromised during the boot up process for example.
There is also mediated access, which is based on centralizing security controls to protect asset groups or security domains. So basically it’s firewalls, application layer gateways, and other sensors working on behalf of the assets they’re supposed to protect, they also mediate these trust relationships between the security domains as well as the directory trust between the servers in the same directory.
And the last but not least is accountability, which means that everybody should sign off on an acceptable use policy. Even administrators are going to be accounted for and traced by using accounting mechanisms, auditing, penetration testing, vulnerability analysis, and ongoing security testing.
Defense-in-depth
Here we see an example of that medieval castle we were talking about earlier, where you have obviously bollards, and moats, and drawbridges, and all these different ways to have different layers to protect the keep – which is you know where the king and queen are deep inside the castle. So this idea has been around for centuries and, so if we think about our castle being the inside network there, our castle will be our database, our datacenter – where all of our mission-critical servers and services are – the server room, the datacenter, that would be our keep.
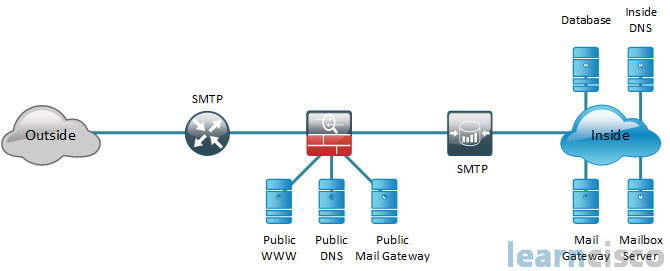
You can see from the outside network, and what we’re talking about here is just E-mail, SMTP. We’ve got a perimeter router which has security services on it. Behind that we have a firewall and that firewall is doing stateful and stateless packet inspection, also application inspection and control. We’ve got a DMZ with three servers down there, a public web server, public DNS, and public mail gateway which is kind of a relay to an inside mail gateway in a server farm or a datacenter. We’ve also got a firewall behind that which is doing filtering or inspection of SMTP as well. And, so on the inside network, we’ve got those internal resources inside DNS, mailbox servers, mail gateways, databases, don’t forget about DHCP servers as well. So this is a very critical concept, and one that is really at the heart of the way you deliver sys from an operational basis as a security practitioner.
So to elaborate on defense-in-depth, you know, this is a philosophy, it’s a combination of an art and a science, basically, to develop a layered security approach by having multiple security mechanisms – defense-in-depth and defense-in-breadth. So security mechanisms should back each other up. For instance, if you have an IDS or an IPS sensor, it’s inspecting traffic inline, it really should only be inspecting the traffic that gets through the firewall first, okay, but the security mechanisms don’t depend upon each other. So their security doesn’t depend upon factors that they can’t control, so each security component does stand alone.
You also want to eliminate single points of failure or weak links in your systems. You want to have redundant firewalls, redundant sensors, and redundant secure routers and switches. You’re going to defend in multiple places, defend in networks and your infrastructure, protect the local area connection, protect the wide area connection, provide the CIA – Confidentiality, Integrity, and Availability. You want to defend your boundaries – not just the boundary to the outside to the service provider but also boundaries between the core of your network in the datacenter or the server farm, protecting, let’s say, some place that’s not secured like a call center, okay.
Think about protecting your management VLAN as well. You’re going to build layers of defenses. Each mechanism should include both protection measures and detection measures, and you should use robust components. In other words, they can be updated on a regular basis, they can be patched and fixed and made to be stronger on an ongoing updated basis. You also want to have robust key management, okay. You’re going to be using public key infrastructures (PKI), and private keys, shared secret key; so have good robust key management. You also want to think about deploying intrusion detection services and/or intrusion prevention services.
Levels of risk
It’s important to realize that risk management is the building block of information security. It’s a trade-off between the amount of money you’re going to spend to protect your assets and the result of exposing those assets. So, basically, the cost to protect your assets shouldn’t be greater than the value of the asset itself. Now there are exceptions because some things you just can’t put a value on, for example human life, right, but the trade-offs and risk management are based on this building blocks – the assets, the vulnerabilities, the threat agents, and whatever countermeasures or mechanisms you’re putting in place to defend against those threat agents. So there are different values and different scenarios depending upon your business sector; for example, are you in the healthcare business, are you in the financial business, are you a manufacturing firm. So there are some things that are variables that are going to affect your risk management approach.
Managing risk
Our risk management becomes a much more complicated issue when we have thousands of assets with different valuations, both quantitative and qualitative in value at different levels of vulnerability, with a different exposure. It’s a delicate balance of variables and factors that have a constant need to be tuned, and a constant need to be analyzed, and have countermeasures put in place. Information security risk management is the comprehensive thing, okay, a comprehensive methodology that has a lifecycle, and it allows you to frame your risk or establish the context of your risk-based decisions. You also can assess risks, you know how you’re going to respond to them, and you’re going to monitor them on an ongoing basis. So the result of this should be a dynamic organic process that is evolving as internal factors change, as assets are depreciated, as new assets replace old assets, as new vulnerabilities are exposed, as you make modifications to your security policies, as your architecture changes, as new technologies emerge, for example. There are also external factors like governance, and threats, and compliance, things like that.
Our Recommended Premium CCNA Training Resources
These are the best CCNA training resources online:
Click Here to get the Cisco CCNA Gold Bootcamp, the most comprehensive and highest rated CCNA course online with a 4.8 star rating from over 30,000 public reviews. I recommend this as your primary study source to learn all the topics on the exam.

Want to take your practice tests to the next level? AlphaPreps purpose-built Cisco test engine has the largest question bank, adaptive questions, and advanced reporting which tells you exactly when you are ready to pass the real exam. Click here for your free trial.
