Now when it comes time to implement risk management, you’re really going to ask yourself two vital questions. What is the cost benefit analysis of the security system? In other words, are you spending more money to savour an asset or protect an asset that is worth less money, okay? And how might your latest attack techniques play out in your network environment, how vulnerable are you to the latest worm attack or the latest malware outbreak?
So when you design your secure network, you need to understand the business needs of your network. Are you a public or private organization, are you, you know, under the mandate of Sarbanes-Oxley or HIPAA – the security rule, you know, risk analysis – what is the balance of risk versus cost, okay, and it’s a fine line, we have to kind of dance on the head of this pin to find what that is. There is also the security policy – how does this tie into your written security policy, your standards, your policies, your guidelines; what are industry best practices, are you following reliable recommended best practices for your business sector. And security operations, which ones are going to be best for your solution, incident response, monitoring, maintenance, auditing – all these things are going to come into play.
You know if I think back to the early 1990s, I think about the reasons why people were creating viruses and other types of malware, it was really just kind of for notoriety okay, they could kind of show off their technical expertise, but hackers or malicious crackers have gone beyond just looking for attention. They’re highly motivated now by financial gain and theft of personal information and damage to systems. For example, the Stuxnet worm, which early iteration show that back in 2009, was extremely damaging. It could traverse industrial control systems, it could affect programmable logic controllers disrupting industrial operations.
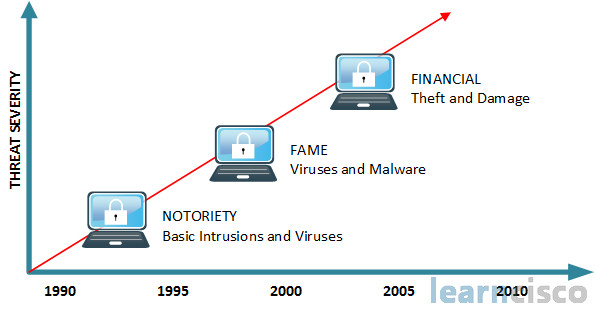
So it was basically at that time called the smartest malware ever invented. So it really just raised everything to a whole new level, and it should be a concern for every government.
Evolving threats
Now in addition to the raising of motivations to financial gain into more destructive levels, we’ve also got just a greater level of expertise with the sense that you can develop these exploits and deliver them in a matter of seconds, and there are widespread activities. There are widespread tools out there like Metasploit among many others that have just programmable modules already built in that make it very easy for somebody to use pre-existing code to deliver these malware threats into our organization. Also with newer devices like handheld devices and PDAs and pads, more mobility solutions especially like in the healthcare field, that adds new threats and vulnerabilities as well. So in the late 2000s, you know, we were able to hack infrastructures, there were Flash threats, there were, you know, worms, they were filling up drives, they were distributed DOS (DDoS) attacks, and of course, damaging viruses and worms, but today we’re looking at things like likejacking which is you know liking on Facebook for example, so social networking is playing a new role. I already mentioned handheld devices and mobility devices. There are widespread compromises to corporate websites, and we looked at the Stuxnet worm, and there is also the Flame virus which is disrupting critical infrastructure in entire countries. There’re exploits of virtualization like people using VMware, or Oracle virtual box, or Hyper-V, exploiting that scenario. The ability to go and do memory scraping not just actually attacking hard drive systems, but using up CPU cycles by going and looking at RAM, volatile scraping of information, hacking hardware at a very low level, okay. And where we had IPv4 from the 90s on, now we’re looking at IPv6 and additional threats. Even though we have IPsec built in to IPv6 with its extensions, we’re still going to look at things like covert channels, man-in-the-middle attacks, and especially attacking dual stack deployments. Organizations and service providers are using IPv6 and IPv4 in concert together during transitional phases.
Recent security challenges
I’m always a bit reluctant to talk about trends and emerging technologies, especially when we’re writing some training at a certain particular point in time because you never know six months from now something can change or there is a new technology, there is bleeding edge technology. So there’re obviously some new paradigms in information security. I’ve already alluded to mobility. And especially in a healthcare environment, we have what’s called mHealth and BYOD (Bring Your Own Device). That applies to more than just the healthcare industry because bringing your own device and integrating that into your business solution is a trend, and that’s a security hole and a security vulnerability.
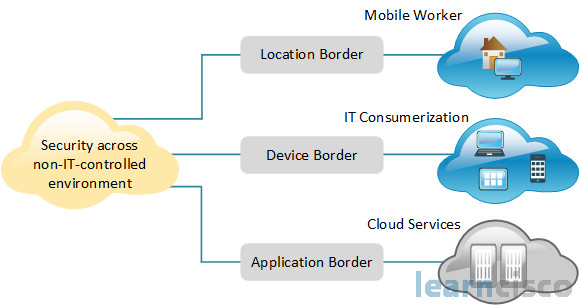
We’ll also see some challenges with cloud computing and cloud services, a lot of companies are going over to that model of Software as a Service and Infrastructure as a Service where they can actually just kind of rent virtual servers somewhere, and, you know, we’ve got the problems with visibility of your data, who owns the data, who controls the physical assets, the encryption keys, you know, how much trust do we have in our cloud partners, what happens if we go into litigation and what happens to the data, what happens to control over the data, while we are going through the process of hashing things out, and of course, just the blurring of the lines between the consumer and the workers, and their basic functionality. So lot of things coming down the pike, and it’s like you’re in graduate school all the time for the rest of your life, because there is always new technology, there are always new threats, and there are always new solutions out there, and it’s very difficult to stay on top of them, but you can do it, and this course is a great way to start.
So we’ve already established the fact that a lot of our attacks out there, a lot of our malware is becoming increasingly financially motivated to identity theft, and to just steal credit card numbers. It’s politically motivated, it’s driven by Botnets, and it’s aimed at critical infrastructure. You don’t want to mention it here but it is a fact that CP is also a huge issue as far as security goes. I don’t want to be insensitive, so CP is an acronym, and the first word is child, okay, so you can kind of fill in what the P stands for. So that’s in there too. Cisco is not mentioning it officially in this course, but that’s a huge issue.
So the top ten Botnets are basically spam and data theft. We’ve recently shutdown one of the biggies, but the Zeus Botnets got to estimated 1.6 million bots or infected hosts. Stuxnet and Flame are targeted in industrial systems. Today I’m sure there’ll be something else. Exploitation of trust is a very powerful weapon. Basically, you’re subverting industrial processes, you’re using social engineering against social networking, exploiting trust between servers and participants in a directory service, things like Koobface, putting false security warnings coming up through web browsers and having users follow through with those, the emergence of tiny URLs which are being used to kind of masquerade longer URLs. Those are definitely handy, but they also can be false, okay, and can redirect you to malicious sites. The attempt to use social engineering against social networking to compromise accounts and like we said likejacking. The Stuxnet worm which is a zero day vulnerability in Windows which can affect what we call SCADA systems. You need to know that acronym, that’s Supervisory Control And Data Acquisition systems, and those are used in a wide variety of different governmental infrastructure facilities not just in the Middle East, but in Western Europe, United States as well, North America. So some key things to think about the realities of our threats out there, increasingly political, and used more and more as a weapon in cyber war, okay, bottom line.
Obviously, from a North American standpoint, threats can be from other countries. Like, you know, well I won’t mention them, but their DNS domain would be .ru, you know, there are the Ukrainians, there’s obviously, the Chinese, and you know, even some of our allies – whose names I won’t mention – are starting to be larger initiators of attacks, okay. Spammers increasingly showing up all over the world. There is a concept known as money muling where individuals are hired as mules, and they are basically setting up fake bank accounts, maybe even their own bank account to help transfer money, and to launder money, and to bring money from a fraud victim’s account to some other location – usually overseas with an ACH transaction or a wire transfer. And they have these mules all over the world. Web malware – obviously on the rise; the more popular the site, the higher the volume of infection. I already mentioned Koobface which attacks more than Facebook, which it’s Koobface really comes from the word Facebook, and there is some Russian gentleman behind that attack which has been very damaging for social networking sites. So lot of interesting things happening right now.
Compliance and effective security
Well, I’ve already mentioned HIPAA, which is part of the healthcare with the privacy rule and security rule. I mentioned Sarbanes-Oxley or SOX, but there are so many others, that your company, your organization maybe under this compliance mandate or governance. There is GLBA – the Gramm–Leach–Bliley Act, of a lot of organizations that are doing financial transactions under PCI-DSS – the Payment Card Industry Data Security Standard. There is also the DMCA – the Digital Millennium Copyright Act, and really several others. So how do we integrate our security posture with these regulations that seem to be just more and more as every year goes by. And some of these are not just based on a country-by-country basis, but a lot of these are enforced worldwide, internationally. And, so you got these certain jurisdictions where these are weekly enforced, others that have better enforcement. So we’re looking forward to some better transparency between the different laws in Asia, and Europe, and North America as this becomes a global thing, but it still brings a lot of challenges for us as security experts.
Our Recommended Premium CCNA Training Resources
These are the best CCNA training resources online:
Click Here to get the Cisco CCNA Gold Bootcamp, the most comprehensive and highest rated CCNA course online with a 4.8 star rating from over 30,000 public reviews. I recommend this as your primary study source to learn all the topics on the exam.

Want to take your practice tests to the next level? AlphaPreps purpose-built Cisco test engine has the largest question bank, adaptive questions, and advanced reporting which tells you exactly when you are ready to pass the real exam. Click here for your free trial.
