Earlier we mentioned the Cisco threat control and containment feature. This is going to comprehensively protect our network through network-wide visibility, a simplified policy control, as well as proactive protection. The control and containment solution will regulate our network access. It’ll isolate infected hosts and servers, it’ll prevent intrusions, it’ll protect our business assets. This is going to counteract traffic like worms, viruses, Trojans, and malware before they can negatively affect our business, based on a centralized policy configuration and threat event management solution. This has really been a core security feature from Cisco for a long time. It really combines the Cisco Adaptive Security Appliance, the Cisco Integrated Services Router, and the Cisco IPS sensor – the 4200 series sensor, or a modular solution like an AIP SSM, or something in the catalyst switch like an IDSM2. These threat prevention mechanisms will be integrated into the fabric of your network. And you’ve also got some very flexible options for deployment, including standalone appliances, or embedded service modules, as well as virtualized devices.
Cisco security intelligence operation
The Cisco Security Intelligence Operation or SIO is a web-based backend security ecosystem that helps detect threat activity. It researches and analyzes threats, it provides real-time updates, and best practices, and guidance to help protect your organization. The SIO has three pillars: threat intelligence (which is the Cisco sensor base), the automatic and human development process (which is the IronPort Threat Operations Center or TOC), and the automated and best practices content that gets pushed to network elements through dynamic updating. It’s a security intelligence center that will baseline the current threat state or status on a worldwide basis and provide your network with valuable information to detect, prevent, and react to threats. It’s an early warning system that correlates threat information from the sensor base that’s analyzed by the talk. It then feeds this information to enforcement elements, for example like IPS sensors for live threat prevention, based on malware outbreaks, day-zero or zero-day attacks, as well as current known vulnerabilities.
Cloud security and data loss prevention
Obviously, you’ve heard the phrase cloud computing, and it really is just a large collection of powerful virtualized servers running on platforms to provide a wide variety of services. But it represents a huge shift in IT, and it’s going into the point where computing is actually kind of a utility. And this provides a lot of innovation potential, a lot of promise, but it also introduces a lot of a new security risks. Here is a list of the top threats to cloud computing:
- Abuse and nefarious use of cloud computing
- Insecure interfaces and APIs
- Malicious insiders
- Shared technology issues
- Data loss or leakage
- Account or service hijacking
- Unknown risk profile
There are actually other risks that aren’t even mentioned here because we don’t want to insult the cloud computing providers. But obviously it gets right down to it – who really owns the data. And we’ve heard that concept in the past that possession is nine-tenths of the law. And so when you sign an SLA with one of these cloud providers, ultimately it’s going to be worked out through the court system or more likely than not arbitration. And there’s a lot of gray area there, so it’s a lot of open field days for the legal industry, but you should know these threats and that sometimes they may outweigh the pros or the positives for your organization.
Cisco ScanSafe and Cisco IronPort
Let’s talk about web security architecture involving the Cisco ScanSafe technology and Cisco IronPort WSA. As you know, malware is a prolific and ubiquitous thing out there. It’s a common vehicle and it shows up now even in cloud services. And so hackers or crackers are exploiting vulnerabilities of open and dynamic web access to distribute their malware, instead of creating their own malicious websites or just leveraging the cloud in other words. So web malware infection from reputable websites is a reality, okay, and it’s actually from a cracker’s standpoint, it’s a more preferred route to infect victims because there’s more transparency there; they can kind of hide themselves in the cloud. So web security architecture from Cisco offers a flexible approach and deployment option for implementing services like URL filtering, content, web content filtering, real-time scanning, web traffic and application control, malware prevention, and other features.
The Cisco ScanSafe web security is a cloud-based solution that will enhance security while also allowing for cost savings, because it eliminates the need to purchase appliances like the IronPort web Security Appliance as an on-premise solution. So you can leverage this cloud-based solution at your service provider. The Cisco ScanSafe web security will analyze every web request to see if it has malicious content, or whether it’s inappropriate or acceptable based on a predefined security policy. This is also a pretty good countermeasure against day-zero or zero-day threats as well. Cisco ScanSafe web security is actually an engine that’s powered by outbreak intelligence, which is basically a correlated detection technology, based on automated machine learning heuristics and what we call “scanlets”. Outbreak intelligence will build a detailed view of every web request, and it’s associated security risk to make sure that your ScanSafe customers are using the World Wide Web in a safe fashion.
It is possible to integrate ScanSafe with the AnyConnect Client. You can also have Cisco IronPort WSAs on premise. If you combine this with ASAs, it’ll implement Acceptable Use Policies, malware prevention, Single Sign on to your SaaS (Software as a Service) cloud provider as well. Cisco AnyConnect users can use VPN technologies to connect to the corporate network through the ASA, and their identities is then share with the Cisco IronPort WSAs for integrated context-aware web security solutions.
Cisco IronPort e-mail security will provide minimized downtime with e-mail borne malware. It’ll simplify the administration of your corporate mail systems. It also reduces the technical staff overhead while giving them insight into the operation of the mail system. It has a combination of best in-class technologies to protect you against junk e-mail. It also provides Data Loss Protection with a partnership with RSA or RSA e-mail DLP. There is virus defense with the virus outbreak filters, and e-mail encryption tracking and reporting tools with the Cisco IronPort PXE encryption technology. IronPort offers a choice of features and functionality that are available on appliance-based, cloud-based, hybrid, or manage solutions.
Secure connectivity through VPNs
Well, as you can see from the diagram, whether you’re a business partner with the Cisco Integrated Services Router at the top left, or a regional office with the Cisco ASA Firewall, or may be a small office – home office – with the Cisco Virtual Office Bundle, you can connect through points of presence, through telcos, through service providers, using IPsec VPNs or SSL TLS VPNs.
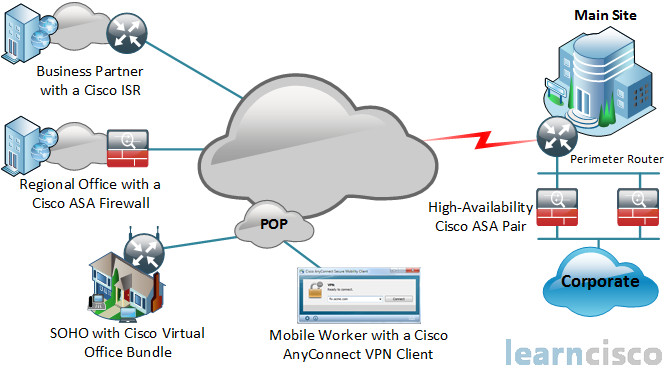
Even the mobile worker with the Cisco AnyConnect VPN Client on their laptop computer can get access to corporate resources behind a perimeter or corporate edge router. You can also be working in concert with a High Availability Cisco ASA pair to provide redundancy and High Availability for their VPN connections.
Cisco Security Manager
If you have to automate, and simplify, integrate your network management, then Cisco is going to have some great solutions for you with some tools that they provide for availability, responsiveness, resilience, and security. These network management systems will reduce your troubleshooting time and your planning time with your security solutions for voice, wireless, and other management. You’ve got device managers embedded into devices in the form of HTML content, for example the ASDM can be used as a graphical tool to support your ASA 5500. You’ve got the Cisco Configuration Professional or the CCP, which can be used with your Integrated Services Routers. And the Cisco Security Manager provides scalable configuration and monitoring for all your devices – for firewalls, routers, switches, IPS sensors, and other security components. The CSM uses multiple approaches to security management including device-focused and policy-focused options as well.
The Cisco Security Manager supports firewalls, VPNs, and sensors. It’ll scale to manage large-scale networks with thousands of devices, and you also get a scalability through intelligent policy-based management techniques that help to simply administration across multiple devices. And it’s even an effective solution for a small-to-medium size business with about a dozen devices as well. If you can afford it, it’s not cheap! It also integrates with Cisco Access Control Server (ACS) to provide granular Role-Based Access Control to devices and management functionality. You can also assign specific tasks to different administrators during the deployment of a policy. You also have formal change control and tracking mechanisms for your ITIL and other team coordination features as well. It provides a rich graphical interface for superior ease of use and ease of deployment.
Our Recommended Premium CCNA Training Resources
These are the best CCNA training resources online:
Click Here to get the Cisco CCNA Gold Bootcamp, the most comprehensive and highest rated CCNA course online with a 4.8 star rating from over 30,000 public reviews. I recommend this as your primary study source to learn all the topics on the exam.

Want to take your practice tests to the next level? AlphaPreps purpose-built Cisco test engine has the largest question bank, adaptive questions, and advanced reporting which tells you exactly when you are ready to pass the real exam. Click here for your free trial.
