One thing we’re finding out is that the demarcation point between, you know, where the mobile user or the mobile worker resides and the consumer device – like Bring Your Own Device (BYOD) into the healthcare environment – or the border of applications, let’s say with the cloud services like infrastructure as a service and software as a service – has really blurred the boundaries. It’s dissolved the borders and forced us to extend security over non-IT controlled environments. As a result, our networks face an increased demand to connect anyone (any device), anywhere, at anytime. This includes partners, customers, and suppliers. So our location border – our enterprise border – is being constantly blurred by ongoing changes to our workplace experience, or by so many different users combining their work-related activities and personal activities on singular devices.
Now here is an interesting graphic. We can see that on the left-hand side, we’ve got our policy, which is going to be governance over our corporate IT (our applications, and our data), our corporate office including the branch office as well (which is always going to be under our written security policy), and that is kind of our logical corporate border.
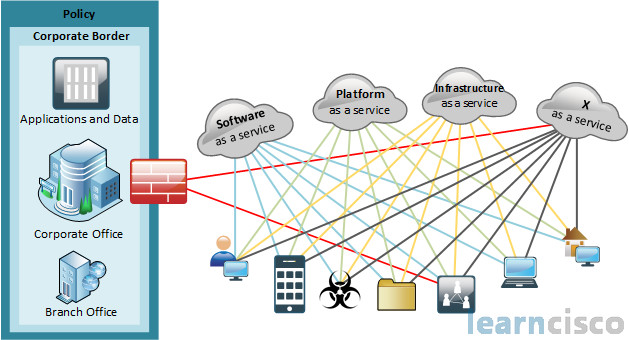
However, the physical corporate border extends beyond just the firewall – as we see there – as we include different cloud services like Software as a Service (SaaS), Platform as a Service (PaaS), Infrastructure as a Service (IaaS), and really anything else you can think of coming down the pike. So this is a changing paradigm where you have to have this kind of seamless context to where service all over the world, all over the globe, and again as part of the cloud. Now this access of anytime, anywhere, using any device, changes the rules for network management and security. We still have to a make sure we have scalability, availability, performance, and other deliverables. But it’s a much more complex scenario for our IT organizations, especially when security is concerned.
Cisco Borderless Networks Architecture
The Cisco borderless network security architecture is going to have several different integrated components, the first being the borderless end zone. That sounds like a very interesting way to play football, but that’s not what it is. This is basically using security controls that are focused on protecting end devices and preventing intrusion to and from these end hosts, for example malware, viruses, Trojans, other types of thing are very common. The borderless end zone is built to detect these threats and eradicate them, or at least to have countermeasures on the network in place. As users connect for multiple location, the network can react to behavior-suspicious activities by basically limiting access based on the security posture of the connecting endpoint. This will lower the impact of endpoint-based threats and then help containment if there are outbreaks, for example.
There is also borderless Internet. This is implemented by scanning and enforcement engines, which are deployed onsite and offsite managed by our organization, but also in partnership with different cloud providers, like for example Trend Micro. These scanning and enforcement engines will look at network content all the way from Layer 2 up to the Application layer. And this basically takes on the role of a firewall, an IDS, IPS, network proxy, application layer gateway, and so on. They’re going to be located throughout the corporate network, and they’ll also be relying on cloud-based services for intelligence, real-time updates, and scanning support for those mobile users, as well as remote offices, and public network resident devices, or Supervisory Control And Data Acquisition (SCADA) systems that we find as part of the United States infrastructure, for example.
Then you have the borderless datacenter. This is basically a special area, okay, because we’re moving to the cloud and virtualization. The borderless architecture will leverage existing infrastructure components – like ASAs, IPS sensors, and switches such as Nexus switches – as well as layering virtualized components on top of security solutions for cloud services. There is also the Policy Management layer. Here, security policy is managed in centralized locations and then enforced through the network, based on context specific variables. For instance, an employee on an untrusted network in London will look at their e-mail through Outlook web access; then they can view messages, but they won’t be able to download attachments. That’s just one simple example.
Borderless end zone
Let’s talk more about the borderless end zone. Each major component here has its particular benefits. It offers deployment flexibility and strong security services in multiple facets as users connect to our corporate network. PCs and mobile devices are obviously big players in borderless network security. All the endpoints authenticate themselves to the network and then will submit to a health and configuration check before they get access. This would be applicable to employees, as well as contractors, vendors, large customers, and third-party users in general. Once they get access to the network, endpoints – endusers – will get access to specific applications and data, based on their role, their location, the time of day, and other factors. It won’t require multiple authentications though. Instead, the network will understand if a user is working from an office desk, a home PC, or an untrusted network anywhere in the world. The network will then enforce policies for access control, data confidentiality, as well as encrypted transport. And then finally, endpoints will continue to have their onboard security defences. But this will involve from current FAT client software to a cloud-based model – especially for mobile devices – and bring your own device (BYOD) scenarios, like healthcare.
The Cisco AnyConnect Client is one of the building blocks of this particular architecture, leveraging secure socket layer in VPNs, SSL VPNs. Then of course, we have our enforcement engines on the other side of the equation, this makes up our security array. Cisco has a strong product line including firewalls, IPSs, web security, as well as e-mail security.
Now by combining our corporate array of scanning technologies and enforcement engines along with intelligent endpoints, we’ll be delivering an integrated, collaborative adaptive security solution. And this is a lot different than we’ve seen before in the past, where you had function-specific products that were basically generating islands of security, which were basically constrained by independent threat, systems, and policy management. So the Borderless network architecture is going to demand a high-level of teamwork, integration, cooperation, and synergy, reminiscent of a symphony orchestra according to Cisco, okay, where individual instruments come together for a common symphony, right. So the borderless architecture allows corporate LANs and WANs to coordinate activities with service provider networks, cloud services, distributed endpoints, and the global Internet itself. So no single vendor has all the security products or resources to solve this challenge, it requires ingenuity and collaboration. And Cisco partners with leading security and network vendors, like Trend, will extend the reach of the system beyond the confines of our corporate networks.
Borderless datacenter
Let’s talk next about the borderless datacenter component of our architecture. Here we’re going to find solutions that basically adapt to our datacenter environments. Here we see the progression of service deployment when you have a heavily virtualized environment, for example using something like VMware, or Oracle, or even Microsoft’s Hyper-V.
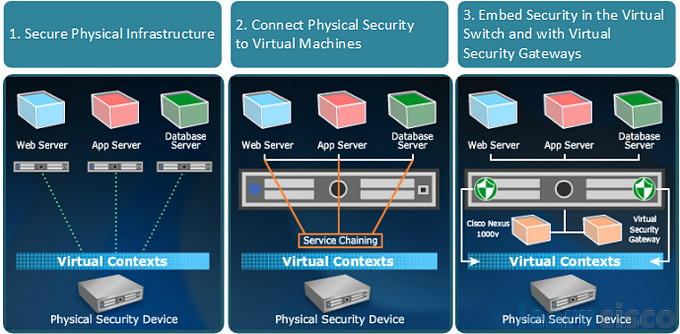
The virtual appliances are going to offer trusted access to virtualized datacenters in cloud provider environments and enterprise environments that are going to this cloud service. They also meet the virtualization requirements of our dynamic policy-driven operation, the enforcement of mobility, and scaling out deployment for dense multi-tenancy for service providers. Also, network connectivity is virtualized and embedded into virtual machines. Virtual switches connect virtual machines within a single physical device. This integrates network switch ports into the hypervisor, for example Cisco Nexus 1000V is a virtual switch. An example of this architecture is the Cisco Virtual Security Gateway (the VSG) – a security virtual appliance that leverages the Cisco Nexus switch to offer zone-based trust services to virtual machines. Cloud providers can then leverage the virtual gateway to enhance their multi-tenant scaling and also create additional revenue by offering security and monitoring services to their customers, so obviously this is a service provider solution here. The VSG will enable a broad set of multi-tenant workloads with varied security profiles to share a common infrastructure of computing onsite. And by associating one or more virtual machines into distinct trust zones, the VSG will ensure that access to the trust zones is monitored and securely controlled through policy.
Our Recommended Premium CCNA Training Resources
These are the best CCNA training resources online:
Click Here to get the Cisco CCNA Gold Bootcamp, the most comprehensive and highest rated CCNA course online with a 4.8 star rating from over 30,000 public reviews. I recommend this as your primary study source to learn all the topics on the exam.

Want to take your practice tests to the next level? AlphaPreps purpose-built Cisco test engine has the largest question bank, adaptive questions, and advanced reporting which tells you exactly when you are ready to pass the real exam. Click here for your free trial.
