Security is no longer an option in wireless LANs; it is an organizational requirement. In this lesson, we are going to describe the common threats to wireless LANs and describe how we have evolved to offer the current best practices for mitigating those threats. Among the solutions: 802.1x for access control and Wi-Fi protected access for confidentiality, integrity, and end point authentication.
Wireless LAN Security Threats
Several factors affect wireless security. For starters, the ubiquity of the technology makes it a good candidate for tax, only we think of the shear numbers. The lower cost of technologies like 802.11b and g make it a more universally adopted technology and, therefore, there will be more unsecure WLANs to choose from.
Malicious attackers can exploit wireless networks with readily available tools to scan for vulnerabilities; in fact, scan for wireless networks in the first place and then exploit vulnerable technologies like WEP or Wired Equivalent Privacy, the encryption algorithm used initially and traditionally for confidentiality, integrity, and authentication in wireless networks. Scanning for wireless networks is known as wardriving, which means driving around with a laptop and a suitable client to find 802.11b, g, or a networks to exploit. Unsecured networks with no encryption confidentiality are easy to exploit, but so are networks that give you the illusion of security with already vulnerable and outdated protocols like WEP. Rogue access points will start claiming packets.
These are devices that are not registered and unknown and may interfere with normal network operations that may actually be used for denial of service attack or simply to gather information and enumerate the network. This can actually be installed and set by the organization’s employees for the sake of mobility and universal access.
In protecting and securing wireless networks, we should apply similar methodologies and design models as we apply to other networks, but this time, we need to be aware of the inherent vulnerabilities of wireless networks and it is nothing more than tradeoff. If we want to have universal access mobility, then we are going to be less secure and so we are going to have to tune up our security policy. The good old CIA model is a good starting point.
CIA stands for confidentiality, integrity, and availability. Especially in wireless networks, we want to protect data as it is transmitted and received and we want to provide encryption mechanisms so that malicious or unwanted users cannot see our information, but we also want to provide integrity and make sure that they cannot change it and endpoint authentication to ensure that only legitimate clients can associate with trusted access points.
This point is a matter of both clients and access points. We want to make sure that connecting devices are legitimate, but we also want to make sure that legitimate clients are connecting to the right access points and not rogue access points. Most of the availability issues in wireless networks are related to denial of service attacks and malicious activity and so if that is a case, intrusion prevention systems are a good tool to start not only baselining the network but also tracking and mitigating unauthorized access and network attacks.
Evolution of Wireless LAN Security
The initial implementations of wireless LANs were probably not thought out with security in mind. They provided a basic encryption algorithm, Wired Equivalent Privacy or WEP, which included 64-bit keys and authentication that was not too strong, keys were eventually compromised and it was easy to break the 64-bit keys knowing that soon enough longer keys became available. Computing power of malicious attackers could easily break the key by gathering enough information from the wireless network.
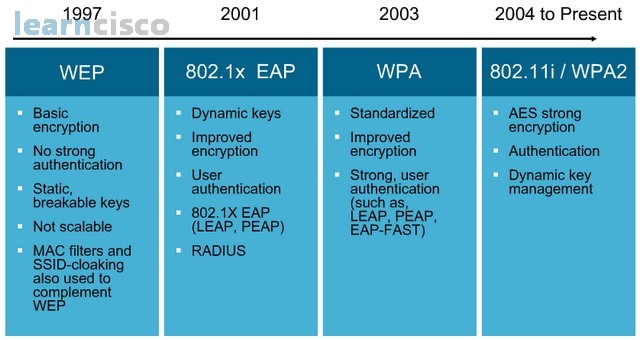
Other vulnerabilities included the fact that the keys were static and this made them both breakable in time and not scalable because you had to configure the keys statically at each connecting device. It became a nightmare for larger organizations.
Several fixes were attempted including MAC filters, which were also too static and not scalable and SSID clocking, which is nothing more than not broadcasting the SSIDs. SSIDs are nothing more than a wireless network name, initially thought of as a password of sorts but then known to be vulnerable as well in terms of security. Next generation included dynamic keys per user, per session using layer 2 authentication mechanisms like 802.1x. This protocol includes the extensible authentication protocol, which was then used to request a procession key from a central AAA server via RADIUS.
The initial flavors of EAP included some proprietary algorithms like LEAP and some others like PEAP or Protected EAP. We are into third generation; the Wi-Fi Alliance tried to standardize security in wireless networks via WPA or Wi-Fi Protected Access. This would mimic the infrastructure of per-user per-session encryption keys, but it would still use WEP as the encryption algorithm and so would the second generation that we just explained and so this would still represent a security vulnerability.
Additional flavors of EAP came about including certain forms of strong authentication with EAP Fast. Our current implementation is WAP2, which includes the enhancements that were added to the 802.11i IEEE standard. Highlights there included the addition of intrusion prevention systems and finally the use of strong encryption algorithms like AES.
Wireless Client Association
Some of the initial vulnerabilities of wireless LANs were related to the very same process of association between clients and access points. The SSID would be used as some sort of a password where it is not. It is simply a network name that is typically broadcasted by access point, so that clients can see it, connect to it. The access point also sends available information in the form of data rates and some other information. Clients would scan all channels and associate with the access point with the strongest signal. The scan would be repeated if the signal weakens and the client needs to associate with the different access point.
It is during the association that clients exchange information with the access point including MAC addresses and security settings. That is why newer flavors of WPA would include protection around the exchange of information and negotiation of parameters. They also added newer forms of authentication because the initial definition would only have open authentication, which does not even include the exchange of credentials and shared key authentication, which defines a static WEP key.
How 802.1X Works on the WLAN
More comprehensive security control for wireless networks is the use of either 2.1x protocols for access control. A 2.1x is an IEEE standard that allows for access control through authentication and authorization of clients going into the network.
It has three main components: the supplicant is the client device trying to connect to the network. The authenticator sits on the enterprise edge and indicates in wireless that this would be an access point. This is a network device that will stop the client request and client traffic and only allow it into the network after successful authentication and authorization. This is a similar to requesting a passport at the airport or folks trying to travel would have to present a passport before going into the airplane. The way this works is by having the authenticator challenge the clients. When it senses that the client is connecting. At that point, the client will provide identity and that identity will be forwarded from the authenticator to a third component, which is the authentication server.
This is typically a AAA server running AAA protocols like RADIUS, and it contains the client database, the user database, and. eventually, it is configured to work with a child protocol of .1x called EAP. This is the extensible authentication protocol and allows the clients to provide credentials in many forms, starting from a user name and password to a digital certificate with encryption and cryptography. So once the authentication server replies with a positive response, then the port can go out of the .1x authentication status and it goes into an effective status that allows clients to go into the network. Client machines need to be configured and need to support the .1x supplicant. This is typically part of the operating system of those machines. The authenticator needs to support .1x, Cisco access points do, and the authentication server would need to be equipped with support for extensible authentication protocol and work as a AAA server using RADIUS.
WPA and WPA2 Modes
WPA or Wi-Fi Protected Access leverages this authentication method of 802.1x plus EAP. It also supports pre-shared keys or PSKs. This defines two levels of authentication, one more suitable for enterprise environments, business, education, government which uses per user per session and authentication keys obtained via the 802.1x EAP exchange. Another one which could be categorized as personal mode, more for home and personal use, which uses a Pre-Shared Key. It does not require the .1x EAP exchange and it can be set simply by configuring a pre-shared key manually.
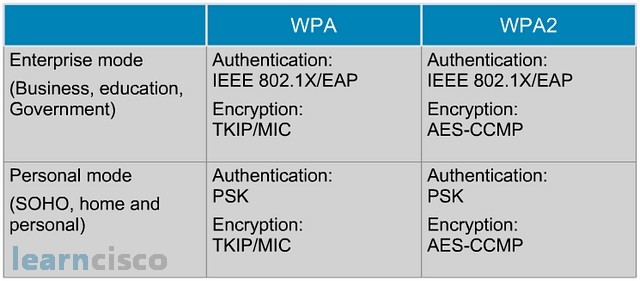
In WPA though, both modes would use WEP as the encryption algorithm and we know that is a vulnerable protocol and so some extra protection was built into WEP in the form of those two protocols, the Temporal Key Integrity Protocol and the Message Integrity Check, which basically added longer rotating keys and some integrity measures. Similar modes exist in WPA2, which is an implementation of Wi-Fi Alliance of the IEEE 802.11i standard. The main difference here is that WEP is no longer the encryption algorithm. The framework is still 802.1x EAP or pre-shared keys, but again the encryption algorithm is now AES or Advanced Encryption Standard.
Our Recommended Premium CCNA Training Resources
These are the best CCNA training resources online:
Click Here to get the Cisco CCNA Gold Bootcamp, the most comprehensive and highest rated CCNA course online with a 4.8 star rating from over 30,000 public reviews. I recommend this as your primary study source to learn all the topics on the exam.

Want to take your practice tests to the next level? AlphaPreps purpose-built Cisco test engine has the largest question bank, adaptive questions, and advanced reporting which tells you exactly when you are ready to pass the real exam. Click here for your free trial.
